Check Out the Best Cyber Security Services in Dubai for Improved Online Protection
Check Out the Best Cyber Security Services in Dubai for Improved Online Protection
Blog Article
Exploring How Cyber Security Functions to Secure Your Online Visibility
In today's electronic landscape, safeguarding one's online presence has actually come to be increasingly vital, with cyber hazards advancing at a worrying rate. Cyber safety and security employs a multifaceted technique, integrating advanced modern technologies like firewall programs, security, and multi-factor authentication to safeguard sensitive details. The intricacy of these systems elevates inquiries concerning their efficiency and implementation. Just how do these innovations interact to create a seamless guard versus cyber dangers? And what role does behavior analytics play in this complex internet of protection steps? These are necessary inquiries that merit additional exploration in our quest for digital security.
Comprehending Cyber Dangers
In the digital landscape, cyber threats stand for a formidable obstacle, calling for a nuanced understanding of their nature and prospective effect. These hazards include a vast array of harmful tasks coordinated by individuals, groups, and even nation-states, targeting delicate data, interrupting operations, or creating reputational damages. Recognizing cyber dangers starts with identifying the various types they take, including malware, phishing, ransomware, and distributed denial-of-service (DDoS) strikes.
Malware, or destructive software program, includes infections, worms, and trojans that penetrate systems to cause or take data harm (Best Cyber Security Services in Dubai). Phishing assaults trick individuals right into disclosing secret information, typically by impersonating as credible entities. Ransomware encrypts victims' information, demanding a ransom for its launch, presenting significant functional and financial risks. DDoS assaults aim to bewilder systems, providing them unusable and interrupting solutions.
Identifying the inspirations behind these threats is vital. Cybercriminals frequently look for economic gain, while hacktivists may seek ideological objectives. State-sponsored assailants may target essential infrastructure for reconnaissance or destabilization functions. By thoroughly recognizing the diverse nature of cyber risks, organizations can much better expect prospective susceptabilities and purposefully allocate resources to bolster their defenses versus these ever-evolving dangers.
Key Cyber Protection Technologies
As organizations make every effort to guard their electronic assets, vital cybersecurity modern technologies play a critical function in fortifying defenses versus cyber risks. IDS screen network website traffic for suspicious activities, while IPS actively obstruct potential risks, guaranteeing real-time defense.
In addition, antivirus and anti-malware remedies remain fundamental in recognizing and alleviating malicious software. They employ heuristic and signature-based methods to detect known and unknown hazards. Endpoint detection and feedback (EDR) systems additionally boost security by offering thorough visibility right into endpoint activities, making it possible for swift incident reaction.
Identification and accessibility management (IAM) technologies make sure that only licensed customers gain access to vital resources, consequently decreasing the danger of unauthorized data gain access to. Multifactor verification (MFA) adds an extra layer of safety, calling for users to supply several verification variables.
Additionally, protection information and event management (SIEM) systems accumulation and analyze safety and security data, offering insights into prospective vulnerabilities and facilitating proactive risk administration. These modern technologies collectively create a robust framework, equipping organizations to preserve a resistant cybersecurity stance.
Function of Firewalls and Security
By regulating incoming and outward bound network web traffic, they protect against unauthorized accessibility to information and systems. Firewall softwares use predefined safety policies to block or allow data packages, successfully shielding delicate details from cyber hazards.
Security, on the other hand, transforms readable information right into an encoded layout that can just be deciphered with a certain cryptographic trick. Encryption is vital for securing sensitive information such as economic data, personal recognition information, and proprietary business details.
With each other, firewalls and file encryption offer an extensive protection device. While firewalls take care of accessibility and shield networks from unauthorized entrance, file encryption safeguards data integrity and confidentiality. Their combined my response application is crucial in mitigating threats and making certain the security of digital assets in an increasingly interconnected globe.

Significance of Multi-Factor Verification
While firewall programs and file encryption develop the foundation of cybersecurity, boosting defenses further needs the application of multi-factor verification (MFA) MFA adds an extra layer of security by calling for users to confirm their identification with two or more different elements prior to obtaining access to sensitive information or systems. These factors generally consist of something the individual recognizes (a password), something the customer has (a safety and security token or smartphone), and something the individual is (biometric verification such as a fingerprint or face recognition)
The value of MFA in protecting on-line existence is paramount in today's electronic landscape. With cyber threats coming to be increasingly innovative, counting solely on standard password-based verification leaves systems prone to breaches. MFA significantly reduces the danger of unapproved gain access to by making it greatly extra tough for cybercriminals to endanger an account. Also if a password is swiped, the additional verification steps serve as a powerful barrier.

Behavioral Analytics in Cyber Safety And Security
Behavior analytics stands for a critical innovation in cybersecurity, supplying an innovative method to threat detection and prevention. By this assessing patterns in user habits, this method identifies abnormalities that might suggest possible cyber hazards.
This innovation is specifically reliable in discovering insider risks and zero-day assaults, which are often missed out on by traditional security systems. Insider hazards, where individuals within a company misuse accessibility benefits, can be especially harmful and difficult to spot. Best Cyber Security Services in Dubai. Behavior analytics gives a layer of examination that can catch subtle discrepancies in actions, such as uncommon gain access to patterns or data transfers, before they escalate right into considerable safety and security events
Moreover, the dynamic nature of behavior analytics allows it to adapt to evolving dangers, giving continuous defense as cyberattack strategies alter. As organizations increasingly depend on digital frameworks, including behavioral analytics into cybersecurity techniques makes sure a resilient protection, maintaining and securing sensitive information rely on digital interactions.
Final Thought
To conclude, the complex approach of cyber security, including innovations such as firewalls, encryption, multi-factor authentication, and behavior analytics, plays an essential function in shielding on the internet presence. By filtering system website traffic, safeguarding information transmission, requiring several verification approaches, and checking customer activity for anomalies, these technologies jointly address the complexities of modern-day cyber risks. This split protection not only safeguards personal and monetary info however likewise makes sure constant security in an ever-evolving digital landscape.
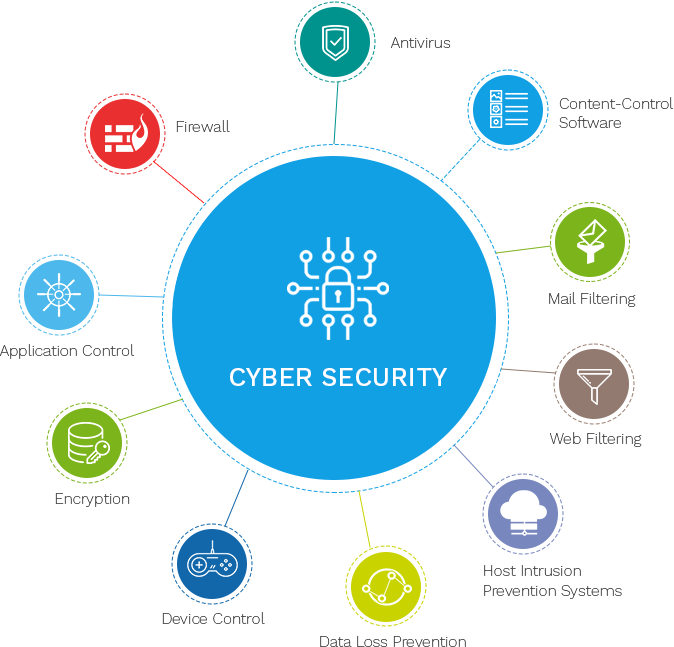
As organizations aim to guard their digital assets, vital cybersecurity technologies play a vital role in strengthening defenses versus cyber hazards. Firewall softwares utilize predefined safety and security regulations to block or allow data packages, properly protecting this website sensitive info from cyber hazards.This innovation is specifically effective in spotting expert hazards and zero-day assaults, which are usually missed out on by conventional protection systems. By filtering system website traffic, safeguarding information transmission, requiring multiple verification approaches, and checking customer activity for anomalies, these technologies collectively address the complexities of modern cyber hazards.
Report this page